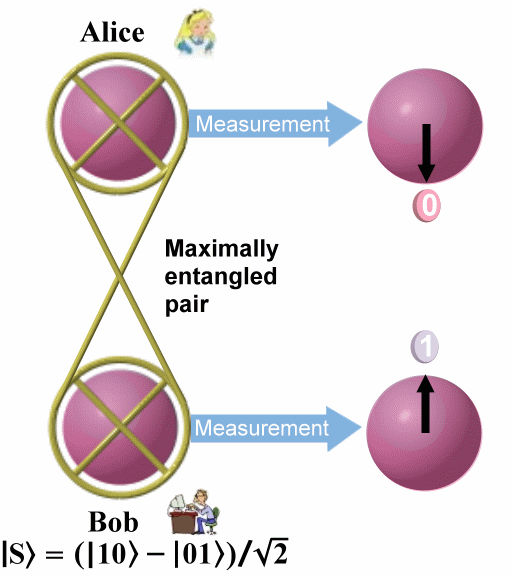
This is only one of four possible Bell states into which the two particles can be entangled. The state given in Eq.(8) distinguishes itself from the others by the fact that it changes sign upon interchanging particle 1 and 2. This unique anti- symmetric feature plays an important role in the experiment.
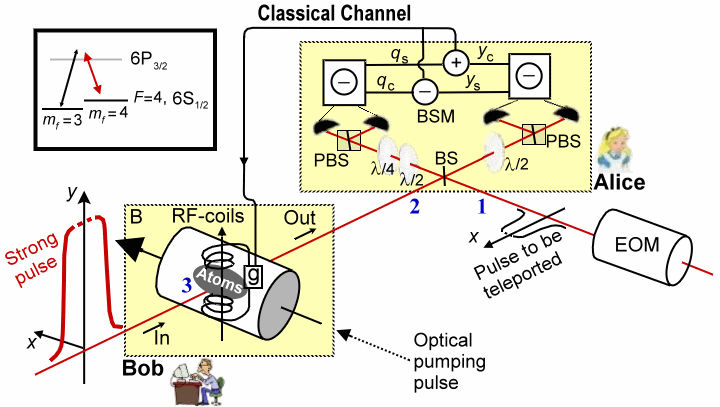
According to the rule of quantum physics once particles 1 and 2 are projected into |f 12, particle 3 is instantaneously projected into the initial state of particle 1. (See top portion of Figure 13-19.) This is because when we observe particles 1 and 2 in the state |f 12, particle 3 is instantaneously projected into the initial state of particle 1. (See top portion of Figure 13-19.) This is because when we observe particles 1 and 2 in the state |f 12 we know that whatever the state of particles 1 is, particle 2 must be in the opposite state. But we had initially prepared particle 2 and 3 in the state |f 12 we know that whatever the state of particles 1 is, particle 2 must be in the opposite state. But we had initially prepared particle 2 and 3 in the state |f 23, which means particle 2 must be in the opposite state of particle 3. This is only possible if particle 3 is in the same state particle 1 was initially. The final state of particle 3 is therefore: 23, which means particle 2 must be in the opposite state of particle 3. This is only possible if particle 3 is in the same state particle 1 was initially. The final state of particle 3 is therefore:
|f 3 = a |1 3 = a |1 3 + b |0 3 + b |0 3 ------ (9) 3 ------ (9)
Note that during the Bell-state measurement particle 1 loses its identity because it becomes entangled with particle 2. Therefore the state |f 1 is destroyed on Alice's side during teleportation. 1 is destroyed on Alice's side during teleportation.
The transfer of quantum information from particle 1 to particle 3 can happen instantly over arbitrary distances,
| | hence the name teleportation. Experimentally, quantum entanglement has been shown to survive over distances of the order of 10 km. In the teleportation scheme it is not necessary for Alice to know where Bob is. Furthermore, the initial state of particle 1 can be completely unknown not only to Bob but to anyone. It could even be quantum mechanically completely undefined at the time the Bell-state measurement takes place. This is the case when particle 1 itself is a member of an entangled pair and therefore has no well-defined properties on its own. This ultimately leads to entanglement swapping (See lower portion of Figure 13-19).
A complete Bell-state measurement not only give the result that the two particles 1 and 2 are in the antisymmetric state in Eq.(8), but with equal probabilities of 25% we could find them in any one the remaining three Bell states. When this happens, the state of particle 3 is determined by one of these three different states. Therefore Alice has to inform Bob, via a classical communication channel, which of the Bell state result was obtained; depending on the message, Bob leaves the particle unaltered or changes it to the opposite state. Either way it ends up a replica of particle 1. It should be emphasized that even if it can be demonstrated for only one of the four Bell states as discussed above, teleportation is successfully achieved, albeit only in a quarter of the cases.
|


 and |0
and |0