
| Home Page | Overview | Site Map | Index | Appendix | Illustration | About | Contact | Update | FAQ |
 |
Factoring large numbers is the basis for a powerful method of information protection. It utilizes a technique called public key cryptography. For example (see Figure 09), Alice sends a public key consisting of a large number (equals to the product of two smaller prime numbers) to Bob. Bob uses this public key to scramble or encode the returning message. Alice then decode the message with the private key consisting of the two original prime numbers. Since it is very difficult to factor the public key, the information is secure, that is, until the arrival of the quantum computing age. |
Figure 09 Encryption |
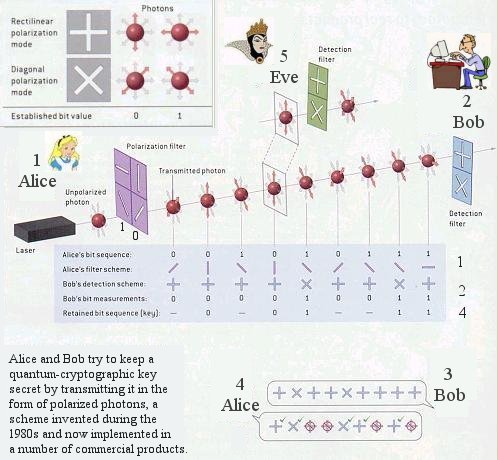 |
Recalling that data encryption is used to protect messages and files from prying eavesdroppers. In its simplest form, a coded message can be created in which each letter is substituted with the letter that is two down from it in the alphabet. So "A" becomes "C", "B" becomes "D", ... and so on. The recipient was told that the code (key) is: "Shift by 2". He/she can then decodes the message accordingly. Anyone else will only see a garbled message. Modern encryption employs two keys to provide greater security. The sender selects a public-key such as 1525381, which is the product of two prime numbers: 10667 and 143. This key is used to convert a block of text via an algorithm (a formula for combining the key with the text). The recipent must used a private key such as 10667 to decode the encrypted text in the reverse process. The security of public-key cryptography depends on factorization - the fact that it is easy to compute the product of two large numbers but extremely hard to factor it back into the primes. |
Figure 10 Quantum Encryption |
But the advent of the quantum information era - and, in particular, the capability of quantum computers to rapidly perform monstrously challenging factorizations - may portend the eventual demise of such cryptographic scheme. (see footnote 3 for more detail of the public key security scheme). |
 |
China has launched a "quantum satellite" on August 16, 2016 (Figure 12a). It carries three experiments on board - the quantum encryption, entanglement, and teleportation. All of them are the extension of ground based testings to outer space about 500 km above ground. The environment is much more suitable but it requires very precise aiming at such long distance and with moving object. The satellite |
Figure 12a Quantum Satellite {view large image] |
goes by the name of Mozi (¾¥¤l) - the ancient sage reputed to be the first Chinese optician some 2500 years ago. The mission will run for 2 years; many more will follow to organize secure communications throughout the world. See "量子科學實驗衛星". |
 |
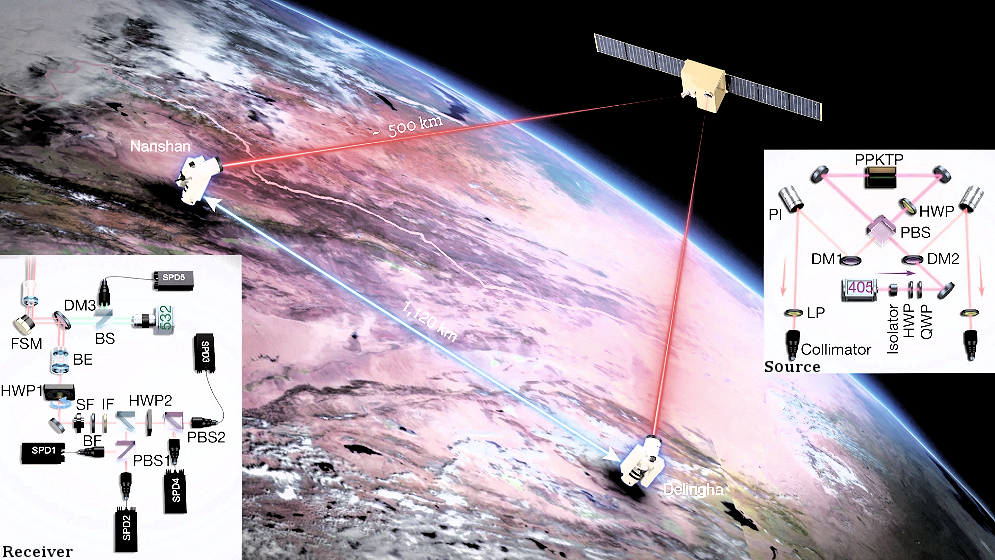 |
In 2020, an experiment with entangled photons achieves a break-through in Quantum Key Distribution (QKD) implementation. The satellite was able to send the entangled pair to 2 ground states 1120 km apart (Figures 12,b,c). They are actually 1.2 m diameter telescopes stowed with advanced optical instruments. The result demonstrates the feasibility of long distance QKD operation secured from prying eyes. |
Figure 12b Quantum Satellite, Mozi [view large image] |
Figure 12c Mozi QKD [view large image] |
See original article "Entanglement-based secure quantum cryptography over 1,120 kilometres", and "量子密鑰有新解方". |
 |
|
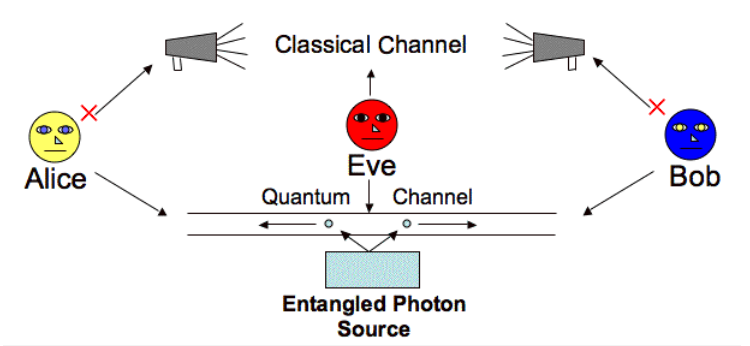
Figure 12e from Entanglement to Measurement [view large image] |
 |
|
Figure 12f[view large image] Mozi Entanglement Exp. |
|
 |
 |
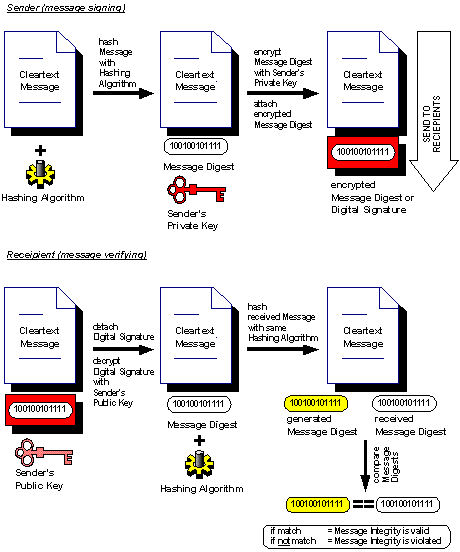 |
known by the recipient only. The two keys are given (by the web hosting company for example) in the form of exponents (two different prime numbers, a shorter one for the public key, a longer one for the private key) and a common 1024 bits modulus. 2. Certificate Authority - The keys alone do not guarantee secure communication unless it can prove the owner's identity without doubt. This is the role played by the certificate authority (CA), which is (similar to the passport office) the agent to certify the credential of the keys. As shown in Figure 14, the public key together with other information are submitted to the registration authority (RA), |
Figure 14 Certification Processing [view large image] |
Figure 15 Hashing [view large image] |
who in turn obtain the certificate from CA. The owner of the keys can now execute transactions without arousing suspicion from the other end. |